Everything You Need to Know About Digital
Sovereignty



Data regulations are constantly changing, but the bottom line is: it’s up to your business to handle employee and customer information responsibly. Doing so is much easier said than done.
Companies have an average of 17 different apps leveraging customer data alone. Ensuring compliance across each of those apps, and any employee data tech, is a complex task. Consider that 92% of the western world’s data is actually housed in the US, where the laws are often in conflict with European laws, and that task compounds in complexity exponentially.
Digital sovereignty enables your business to effectively and compliantly handle your data. You control what data your business has and where you store it, staying in line with local data regulations.
In this article, you’ll learn what digital sovereignty is, why it’s important, and what you can do to stay compliant.
Digital sovereignty describes a party’s right and ability to control its own digital data. It includes control over a company’s digital environment, including customer and employee data, software, hardware, and other digital assets.
Pierre Bellanger, author of La Souveraineté Numérique (Digital Sovereignty), defines it as follows:
“Digital sovereignty is control of our present and destiny as manifested and guided by the use of technology and computer networks.”
Digital sovereignty consists of two main pillars: data sovereignty and technological sovereignty.
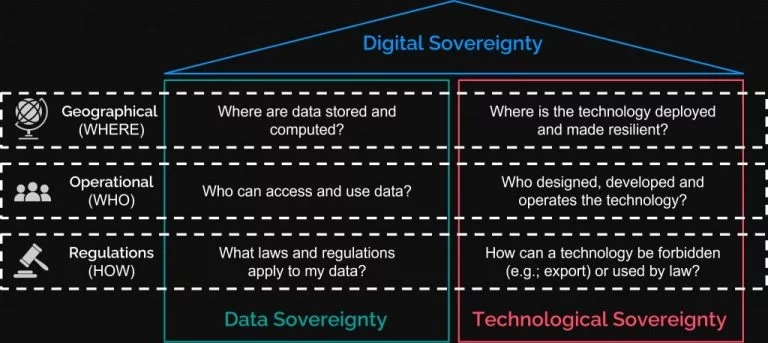
Source: Atos
Digital sovereignty fluctuates as businesses grow and develop, meaning that companies can achieve it to varying degrees. For example, you might have total data sovereignty with locally based servers, but your technological sovereignty is limited due to legacy systems in place.
Ideally, companies should aim for total digital sovereignty. As a business leader, you’ll have total authority over all your data and digital assets, so you can take the right measures to keep it secure.
But it’s not a straightforward process, particularly for businesses in Europe. Before we explain why, let’s cover two important terms for understanding digital sovereignty: digital assets and corporate governance.
A digital asset is a discoverable, owned item of value that your company stores digitally.
For example, a document that outlines a company process would be valuable to the company, but a meme shared in a Slack channel would not.
Here are some examples of digital assets that may be created and owned by the company:
Effectively managing your digital assets is a key part of digital sovereignty; you need to know what data you have, how to store it, and how to use it in line with data regulations. That’s why effectively managing your digital assets is so important (we’ll discuss how to do this in more detail later).
Corporate governance involves effectively managing a company to enable it to do the following:
Essentially, governance ensures that businesses are organized, efficient, and compliant with the law—all of which are key for digital sovereignty.
Recall that nearly all of the western world’s data is stored in the United States. Globally, we rely on tech companies in the US and, to a lesser degree, China to store and manage a huge amount of data.
With so much data storage and processing happening overseas, European governments and policymakers are raising concerns. They want stronger parameters in place to use and store data locally, which will ensure European countries can manage their own data, improve their digital ecosystem, and increase digital sustainability.
To overcome this challenge, European digital sovereignty requires the strengthening of its regulatory autonomy. This means setting its own rules and helping them prevail alongside the dominant players.
Here’s a simplified overview of how this can happen:
Implementing these steps is no easy task, leaving many European businesses still struggling to manage and control their own data.
Take a look at Apple, as an example.
In June 2021, the company announced a Private Relay service. This service encrypts data so that no one (including Apple) can see a users’ online browsing activity.
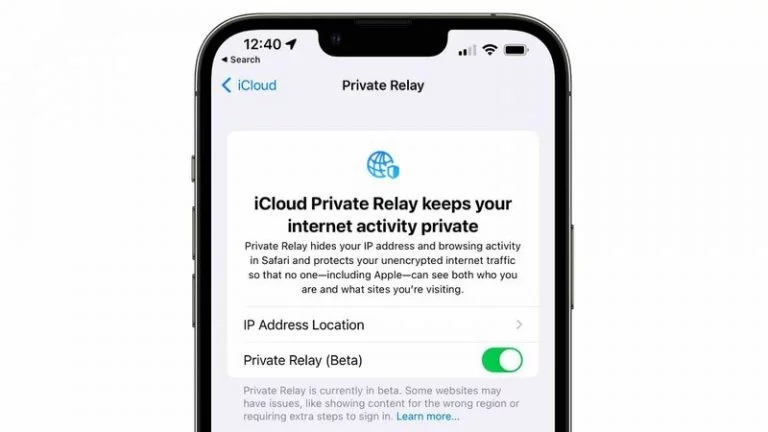
Source: MacRumors
Vodafone, Telefonica, Orange, and T-Mobile sent a joint letter to the European Commission to voice their concerns about the feature.
The group wants Apple to stop using this feature as it’ll prevent them from effectively managing their networks by restricting their access to crucial data.
In other words, Apple’s data privacy move impacts European digital sovereignty.
The good news is Europe is rolling out initiatives to help European businesses gain control of their critical infrastructures.
The Digital Markets Act (DMA) and Digital Services Act (DSA) are in place to create a fairer and safer digital space for businesses. They protect user rights and create a level playing field for businesses to innovate, grow, and compete.
The General Data Protection Regulation (GDPR) is another example. The legislation came into force in 2018 to protect personal data across Europe.
There are also agencies helping companies to take charge of their own data, such as Numspot. Numspot is a joint venture by La Poste, Dassault Systèmes, Bouygues Telecom and Caisse des Dépôts to create a trusted, locally-based cloud server. From mid-2023, French businesses (and even the public) will be able to keep their data in the country where they can keep a better eye on it.
Numspot is one firm in a new wave of data sovereignty companies cropping up in Europe in an effort to help businesses govern their own IT systems and the data they manage.
Established European software companies offering a secure cloud do exist. OVH, for example, is an existing cloud provider in France and a founding member of CISPE (Cloud Infrastructure Services Providers in Europe).
As of 2018, the UK and each European country have data protection authorities that supervise data compliance. In Europe, these authority representatives are organized into a group called the European Data Protection Board (EDPB).
The EDPB members are tasked with:
All of these regulations and initiatives are helping Europe gain control of its digital infrastructure, capacities, skills, and data.
But there are still some hurdles to overcome—which brings us to the CLOUD Act.
The CLOUD Act (Clarifying Lawful Overseas Use of Data Act) is a US federal law.
The law allows US authorities to access electronically-stored data from US companies with cross-border operations (subject to a court order and providing the data is relevant to an ongoing investigation).
This means the US government can access data from US-owned European companies.
For example, companies such as Microsoft, Amazon, and Google are all US-owned, but they have data centers across the European Union (EU). The CLOUD Act also allows countries in the EU to form agreements for exchanging data. Take a look at the agreement between the US and the UK as an example.
But, the CLOUD Act has caused some controversy in Europe because it can restrict digital sovereignty. With so many servers and companies located in the US, European countries are bound to the rules of US law. As a result, they’re unable to achieve digital sovereignty.
Paul van den Berg of the Dutch National Cyber Security Center (NCSC) reported:
“Companies and organizations are actually less and less able to guarantee or ensure that the information they process is sufficiently protected against access by foreign, non-European, powers.”
On top of this, there are claims that the CLOUD Act conflicts with the GDPR.
For instance, let’s say a US company asks for data from their French operation about a group of their customers. To comply with the CLOUD Act, the French office is required to disclose this information—but in sharing this information, the French office is no longer compliant with the GDPR.
Now more than ever, Europe is stressing the importance of using cloud services based in the EU. This ensures that personal data is protected within EU data protection laws and in line with EU values.
Over the last decade, digital sovereignty has become a key element in digital policy discourses. Unsurprisingly, this has had a knock-on effect for businesses.
Cisco found that 76% of globally surveyed consumers wouldn’t buy products from a business they do not trust to manage their data. Furthermore, over one-third (37%) have switched to a competitor because of data privacy practices.
Let’s explore some of the arguments for digital sovereignty for businesses.
Becoming a digital sovereign means managing your own data. You have authority over the data you collect, where you store it, and how you manage it.
This is beneficial for businesses because you’re able to keep better tabs on your data, you’re never locked out of accessing it, and you can see when it’s been completely erased from the system.
You’ll also have a much clearer picture of what information your company keeps in the database. Not only will this help you better structure and organize your existing data, it’ll also help you stay on top of compliance with data privacy laws (more on this later).
It’ll also help you keep on top of your own governance, so you can ensure everything follows your internal privacy practices. If it doesn’t, you have the authority to make the necessary changes immediately.
Risk is inevitable when controlling and regulating your own data. Since you’re the reigning authority on customer information, it’s down to you to ensure you successfully protect that data.
If your business doesn’t follow regulations, you risk penalties, fines, and losing trust with customers.
When data is housed externally, it’s harder (or impossible) to detect nefarious activity, poor data protection processes, outdated storage systems, etc.
The good news is, using a local server or cloud provider makes it easier to follow local data protection rules. A recent study shows that of those IT/IS managers who use a local cloud provider, nearly one-third use it for regulatory compliance and one in five use it to fulfill digital sovereignty requirements.
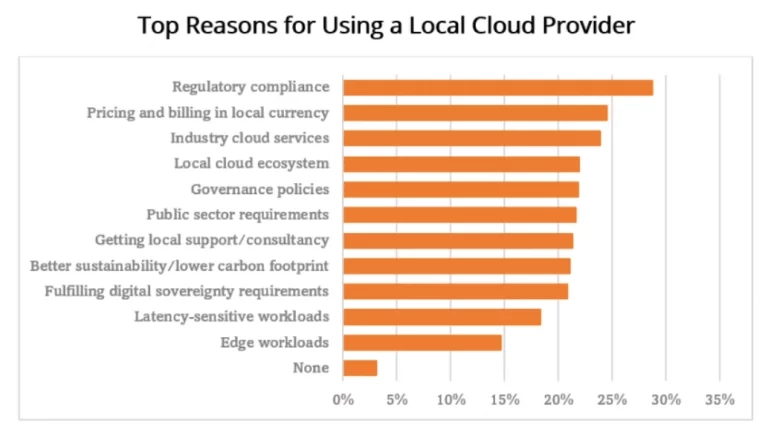
Source: IDC
So, how does a local cloud or service provider help you comply with data privacy rules?
Simply put, storing your data locally gives you easier access to it. It’s already in the country, and you don’t have to worry about your data having to follow regulations from other countries.
In other words, locally storing your data makes it easier for you to ensure that everything complies with your local privacy regulations. Without this level of transparency, it becomes harder to monitor your data and comply with local regulations.
Embarrassing public data breaches happen all the time. The Covid-19 pandemic caused a huge influx of customers for digital platforms that simply weren’t equipped for it.

Source: Deloitte
Put yourself in your customer’s shoes for a second. How would you feel knowing that a company you trust isn’t following data privacy regulations? Chances are, you’d be concerned about your personal information (like your home address and credit card details).
To build trust, you need to be transparent about how you store and manage customer data.
This is where digital sovereignty comes into play.
By having control of your data and processes, you can provide total transparency to your customers. You can tell them exactly where their data is stored, how you manage it, and what you do with it.
Let’s take a look at some of these best practices for mastering digital sovereignty.
Start by getting yourself up to speed with data regulations and governance set out by your country, governing body, or industry.
How you do this is highly subjective; the regulations you need to follow depend on where your business operates and what industry you’re working in. You’ll need to conduct your own research to make sure you’re abiding by the laws and regulations that apply to your business.
To learn where you need to start and gauge how big of a task this will be, take a look at the European Commission’s rules about the protection of personal data.
If you’re concerned about sourcing the right information, consider either talking to an external data compliance consultant or training an employee to act as the internal data compliance officer. That way, you can rest assured that you’re getting reliable advice on the best practices for data privacy.
With a solid understanding of data regulations and privacy laws, you can review how you use and store data. This should help you understand the granular details of your data collection. From here, you can identify vulnerabilities and pinpoint areas of improvement.
Here are some examples of information you need to analyze:
During this process, it’s important that any digital transformation shouldn’t impact your agility.
In our fast-paced digital age, your business needs to keep up with competitors. If you take too many steps too fast, your efficiency could take a hit.
Take time to determine the best way to implement any changes and work with a change management team if technology updates are significant and productivity is critical.
We’ve already talked about the importance of digital asset management when it comes to digital sovereignty. Now, let’s look at exactly how to do it.
Let’s explore some ways to manage your digital assets effectively:
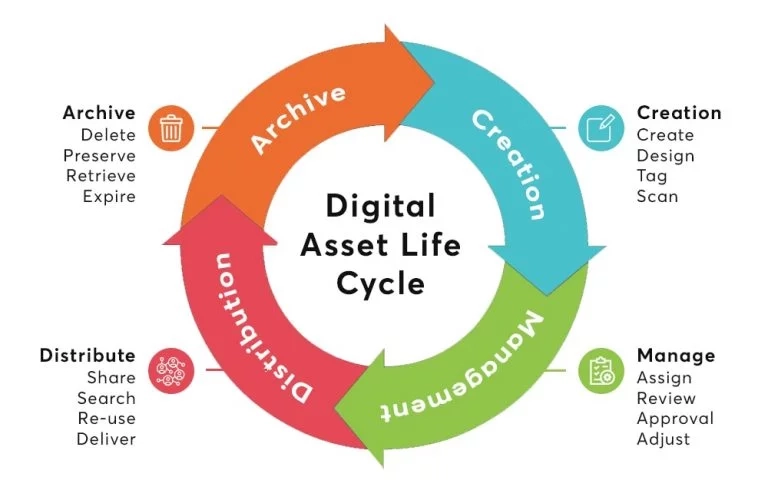
Source: Comparesoft
Apizee is a cloud-based telecommunications platform that helps businesses effectively connect with customers, stakeholders, and colleagues. Using real-time web and mobile communication, businesses can keep in touch both remotely and on-site.
With Apizee, you can provide video customer support, offer private telehealth advice over encrypted video calls, and field service across a variety of devices and platforms.

When it comes to digital sovereignty, using Apizee is a step in the right direction.
We take digital security and privacy seriously. All of our data is stored in Europe, while our research and development teams are in France. We’re also up to speed with the GDPR.
Here’s how we renewed all our systems and processes to abide by the new regulations:
You can also find out more about our data privacy regulations in our privacy policy.
The path to achieving digital sovereignty can be long and complicated. There are plenty of challenges to overcome for full control of all your data assets, but it’s possible.
Today, not many European companies can say they have total control over customer data. With information leaks proliferating, being the sole data authority is a competitive advantage.
Consider Apizee in your move toward digital sovereignty. Our secure video-communication platform focuses on digital customer interaction, visual assistance, and enterprise collaboration. Contact us for a free quote.
Read also :
Claire Boscq, CX Activator and founder of JCX Alliance, shares her unique approach to wellbeing-led customer experience. Discover her vision in this new Apizee CX Voices interview.
[CX Industry Voices] Interview with Claire Boscq
25 Jun 2025
Call Centre Helper’s Xander Freeman spoke to Charles Kergaravat, CMO at Apizee, about the rise of video chat in customer service.
The rise of Video Chat in customer service
20 Jun 2025
Simon Macklin from Salesforce, explains how AI and human empathy combine to shape the future of CX. Discover insights in the latest Apizee CX Voices interview.
[CX Industry Voices] Interview with Simon Macklin
19 Jun 2025
Interested in our solutions?