Everything You Need to Know About Digital Sovereignty



Data regulations are constantly changing, but the bottom line is: it’s up to your business to handle employee and customer information responsibly. Doing so is much easier said than done.
The uncomfortable truth is that most European organizations don’t just outsource tools—they outsource critical digital control. In today’s geopolitical climate, that’s no longer a theoretical debate. It’s why digital sovereignty is climbing fast on the priority list for governments and executives across Europe.
The numbers explain the urgency: about 80% of European corporate spending on cloud and software goes to U.S. providers—roughly €284B per year—and those flows are associated with nearly 2 million jobs on the U.S. side of the Atlantic.
Digital sovereignty gives your business a way to regain control: what data you have, where it sits, and under which rules it can be accessed—so compliance is realistic, and resilience isn’t optional.
In this article, you’ll learn what digital sovereignty is, why it’s important, and what you can do to stay compliant.
Digital sovereignty describes a party’s right and ability to control its own digital data. It includes control over a company’s digital environment, including customer and employee data, software, hardware, and other digital assets.
Pierre Bellanger, author of La Souveraineté Numérique (Digital Sovereignty), defines it as follows:
“Digital sovereignty is control of our present and destiny as manifested and guided by the use of technology and computer networks.”
Digital sovereignty consists of two main pillars: data sovereignty and technological sovereignty.
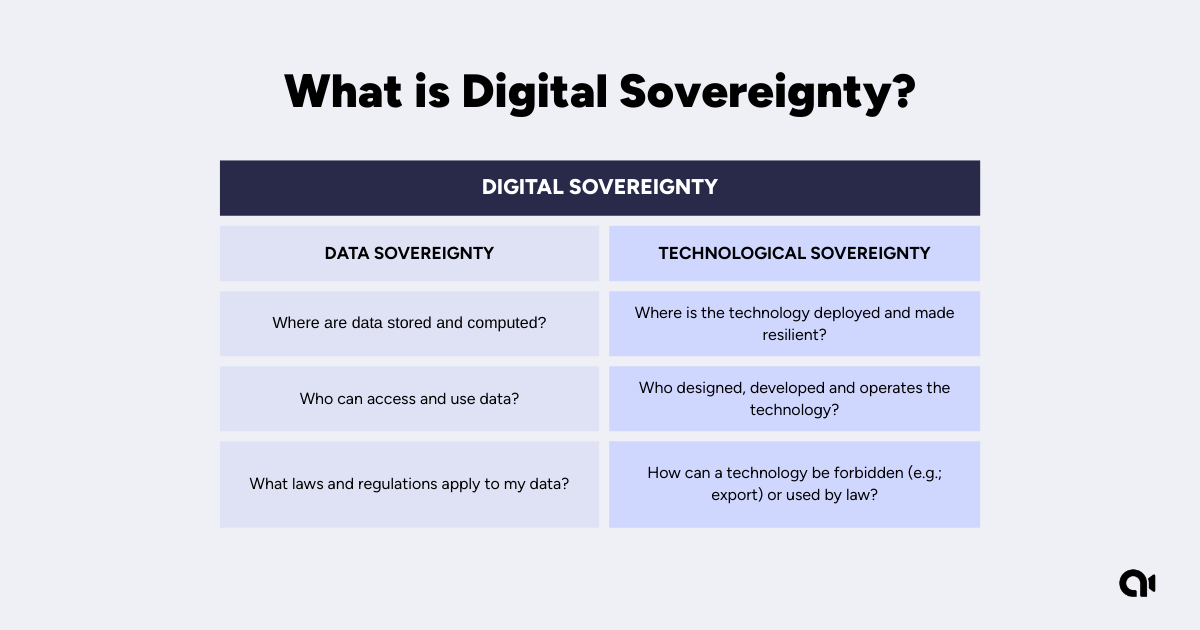
Source: Atos
Digital sovereignty fluctuates as businesses grow and develop, meaning that companies can achieve it to varying degrees. For example, you might have total data sovereignty with locally based servers, but your technological sovereignty is limited due to legacy systems in place.
Ideally, companies should aim for total digital sovereignty. As a business leader, you’ll have total authority over all your data and digital assets, so you can take the right measures to keep it secure.
But it’s not a straightforward process, particularly for businesses in Europe. Before we explain why, let’s cover two important terms for understanding digital sovereignty: digital assets and corporate governance.
A digital asset is a discoverable, owned item of value that your company stores digitally.
For example, a document that outlines a company process would be valuable to the company, but a meme shared in a Slack channel would not.
Here are some examples of digital assets that may be created and owned by the company:
Effectively managing your digital assets is a key part of digital sovereignty; you need to know what data you have, how to store it, and how to use it in line with data regulations. That’s why effectively managing your digital assets is so important (we’ll discuss how to do this in more detail later).
Corporate governance involves effectively managing a company to enable it to do the following:
Essentially, governance ensures that businesses are organized, efficient, and compliant with the law—all of which are key for digital sovereignty.
Europe doesn’t just use digital services—it runs on them. And a large share of the cloud, software, and infrastructure European organizations depend on is built and operated by non-European companies.
With geopolitical tension rising, that dependency is no longer framed as a simple procurement choice. Policymakers and business leaders across Europe are now treating it as a continuity risk: what happens if a critical digital service is restricted, disrupted, or governed by rules outside Europe? France’s newly launched Indice de Résilience Numérique (IRM) is built around that exact question—measuring how dependent an organization is on foreign technologies and how well it could operate if key services were cut.
And the “deal” is not only about where data sits. It’s also about jurisdiction and control. Under oath in the French Senate, Microsoft France’s Anton Carniaux was asked whether he could guarantee French citizens’ data could not be transmitted to U.S. authorities without French government approval. His answer was blunt: “No… I cannot guarantee that.”
That’s why European digital sovereignty increasingly means strengthening regulatory autonomy and building real alternatives—so European rules can actually prevail alongside dominant global players. The EU has even created the Digital Commons European Digital Infrastructure Consortium (DC-EDIC), described as a strategic instrument to reduce dependency on “a small number of global platforms,” and to act as an incubator and one-stop shop to help deploy open-source solutions at continental scale.
Here’s a simplified overview of what this looks like in practice:
Implementing these steps is no easy task, leaving many European businesses still struggling to manage and control their own data.
Take France’s Health Data Hub as a recent example. The government announced a migration toward a secure, resilient cloud solution not subject to extra-EU legislation, with a selection process targeting a provider aligned with the SecNumCloud label (which explicitly excludes hyperscalers like Microsoft, Amazon, and Google).
In other words, digital sovereignty isn’t a theoretical debate anymore—it’s showing up in procurement decisions, platform regulation, and national infrastructure choices across Europe.
The good news is Europe isn’t just talking about sovereignty anymore—it’s building rules, measurement tools, and procurement paths that push organizations to reduce dependency on extra-EU tech.
First: regulation.
Europe has put hard rules in place to rebalance power in the digital economy. The Digital Markets Act (DMA) and Digital Services Act (DSA) aim to create a fairer and safer digital space—protecting user rights while giving businesses a more level playing field to innovate and compete. And the direction of travel is clear: in January 2026, President Emmanuel Macron called for the EU to deepen its digital rulebook in the face of U.S. pushback, arguing Europe needs to “act as Europeans” and assert a real “power posture” on digital policy.
Second: political direction is getting much more explicit.
At France’s “Rencontres de la souveraineté numérique” in January 2026, the minister for digital affairs Anne Le Hénanff called for a “préférence européenne” and highlighted the “vulnérabilités” France faces by relying on extra-European digital services—especially given “unilateral decisions taken by foreign actors.” She also urged French companies to commit more strongly to French and European solutions, saying the state would be “exemplary.”
Third: Europe is trying to make dependency measurable—and actionable.
France is moving toward tools that map and quantify reliance on non-European services (observatory + resilience-style scoring). That matters because sovereignty becomes real when it changes how procurement and risk management are done—not when it stays a slogan.
Fourth: building European cloud options.
France-backed initiatives like NumSpot (Docaposte/La Poste, Banque des Territoires, Dassault Systèmes, Bouygues Telecom) are part of a broader wave of “trusted” or “sovereign” cloud offerings aimed at hosting sensitive workloads under European control. NumSpot announced commercialization of its platform starting Q1 2025.
Established European providers also exist—OVHcloud, for example, has long positioned itself around European hosting and is a founding member of CISPE.
Fifth: scaling European “digital commons.”
At the EU level, the Commission created the Digital Commons European Digital Infrastructure Consortium (DC-EDIC) to reduce dependency on a small number of global platforms and help deploy open-source solutions across Europe—acting as an incubator and one-stop shop with funding pathways plus technical and legal support.
And the urgency isn’t theoretical. In Germany, reporting based on a survey cited by WELT suggests more than 8 in 10 companies believe they would not survive the next two years if technology imports and digital services were suddenly unavailable—an indicator of how deeply embedded foreign tech has become in day-to-day operations.
All of these initiatives help Europe regain control over its digital infrastructure, skills, and data.
But there are still some hurdles to overcome—which brings us to the CLOUD Act.
The CLOUD Act (Clarifying Lawful Overseas Use of Data Act) is a US federal law.
The law allows US authorities to access electronically-stored data from US companies with cross-border operations (subject to a court order and providing the data is relevant to an ongoing investigation).
This means the US government can access data from US-owned European companies.
For example, companies such as Microsoft, Amazon, and Google are all US-owned, but they have data centers across the European Union (EU). The CLOUD Act also allows countries in the EU to form agreements for exchanging data. Take a look at the agreement between the US and the UK as an example.
But, the CLOUD Act has caused some controversy in Europe because it can restrict digital sovereignty. With so many servers and companies located in the US, European countries are bound to the rules of US law. As a result, they’re unable to achieve digital sovereignty.
Paul van den Berg of the Dutch National Cyber Security Center (NCSC) reported:
“Companies and organizations are actually less and less able to guarantee or ensure that the information they process is sufficiently protected against access by foreign, non-European, powers.”
On top of this, there are claims that the CLOUD Act conflicts with the GDPR.
For instance, let’s say a US company asks for data from their French operation about a group of their customers. To comply with the CLOUD Act, the French office is required to disclose this information—but in sharing this information, the French office is no longer compliant with the GDPR.
Now more than ever, Europe is stressing the importance of using cloud services based in the EU. This ensures that personal data is protected within EU data protection laws and in line with EU values.
Over the last decade, digital sovereignty has become a key element in digital policy discourses. Unsurprisingly, this has had a knock-on effect for businesses.
Cisco found that 76% of globally surveyed consumers wouldn’t buy products from a business they do not trust to manage their data. Furthermore, over one-third (37%) have switched to a competitor because of data privacy practices.
Let’s explore some of the arguments for digital sovereignty for businesses.
Becoming a digital sovereign means managing your own data. You have authority over the data you collect, where you store it, and how you manage it.
This is beneficial for businesses because you’re able to keep better tabs on your data, you’re never locked out of accessing it, and you can see when it’s been completely erased from the system.
You’ll also have a much clearer picture of what information your company keeps in the database. Not only will this help you better structure and organize your existing data, it’ll also help you stay on top of compliance with data privacy laws (more on this later).
It’ll also help you keep on top of your own governance, so you can ensure everything follows your internal privacy practices. If it doesn’t, you have the authority to make the necessary changes immediately.
Risk is inevitable when controlling and regulating your own data. Since you’re the reigning authority on customer information, it’s down to you to ensure you successfully protect that data.
If your business doesn’t follow regulations, you risk penalties, fines, and losing trust with customers.
When data is housed externally, it’s harder (or impossible) to detect nefarious activity, poor data protection processes, outdated storage systems, etc.
The good news is, using a local server or cloud provider makes it easier to follow local data protection rules. A recent study shows that of those IT/IS managers who use a local cloud provider, nearly one-third use it for regulatory compliance and one in five use it to fulfill digital sovereignty requirements.
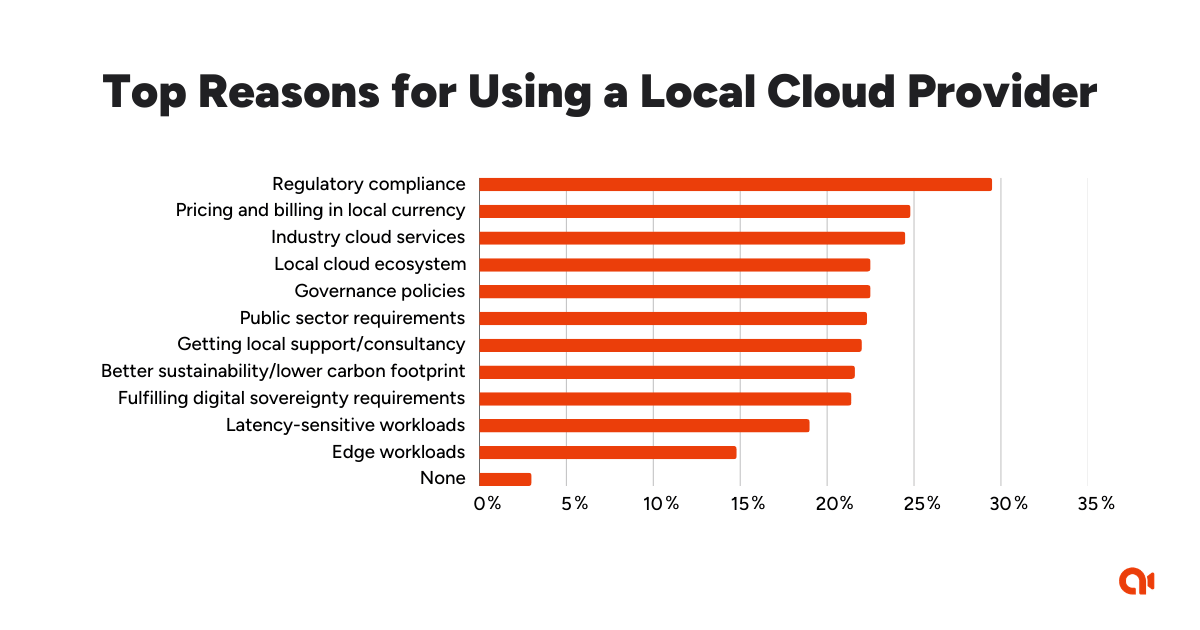
Source: IDC
So, how does a local cloud or service provider help you comply with data privacy rules?
Simply put, storing your data locally gives you easier access to it. It’s already in the country, and you don’t have to worry about your data having to follow regulations from other countries.
In other words, locally storing your data makes it easier for you to ensure that everything complies with your local privacy regulations. Without this level of transparency, it becomes harder to monitor your data and comply with local regulations.
Embarrassing public data breaches happen all the time. The Covid-19 pandemic caused a huge influx of customers for digital platforms that simply weren’t equipped for it.

Source: Deloitte
Put yourself in your customer’s shoes for a second. How would you feel knowing that a company you trust isn’t following data privacy regulations? Chances are, you’d be concerned about your personal information (like your home address and credit card details).
To build trust, you need to be transparent about how you store and manage customer data.
This is where digital sovereignty comes into play.
By having control of your data and processes, you can provide total transparency to your customers. You can tell them exactly where their data is stored, how you manage it, and what you do with it.
Let’s take a look at some of these best practices for mastering digital sovereignty.
Start by getting yourself up to speed with data regulations and governance set out by your country, governing body, or industry.
How you do this is highly subjective; the regulations you need to follow depend on where your business operates and what industry you’re working in. You’ll need to conduct your own research to make sure you’re abiding by the laws and regulations that apply to your business.
To learn where you need to start and gauge how big of a task this will be, take a look at the European Commission’s rules about the protection of personal data.
If you’re concerned about sourcing the right information, consider either talking to an external data compliance consultant or training an employee to act as the internal data compliance officer. That way, you can rest assured that you’re getting reliable advice on the best practices for data privacy.
With a solid understanding of data regulations and privacy laws, you can review how you use and store data. This should help you understand the granular details of your data collection. From here, you can identify vulnerabilities and pinpoint areas of improvement.
Here are some examples of information you need to analyze:
During this process, it’s important that any digital transformation shouldn’t impact your agility.
In our fast-paced digital age, your business needs to keep up with competitors. If you take too many steps too fast, your efficiency could take a hit.
Take time to determine the best way to implement any changes and work with a change management team if technology updates are significant and productivity is critical.
We’ve already talked about the importance of digital asset management when it comes to digital sovereignty. Now, let’s look at exactly how to do it.
Let’s explore some ways to manage your digital assets effectively:
Source: Comparesoft
Apizee is a visual engagement platform that helps businesses effectively connect with customers, stakeholders, and colleagues. Using real-time web and mobile communication, businesses can keep in touch both remotely and on-site.
With Apizee, you can provide video customer support, offer private telehealth advice over encrypted video calls, and field service across a variety of devices and platforms.

When it comes to digital sovereignty, using Apizee is a step in the right direction.
We take digital security and privacy seriously. All of our data is stored in Europe, while our research and development teams are in France. We’re also up to speed with the GDPR.
Here’s how we renewed all our systems and processes to abide by the new regulations:
You can also find out more about our data privacy regulations in our privacy policy.
The path to achieving digital sovereignty can be long and complicated. There are plenty of challenges to overcome for full control of all your data assets, but it’s possible.
Today, not many European companies can say they have total control over customer data. With information leaks proliferating, being the sole data authority is a competitive advantage.
Take control of your digital communications with a secure, sovereign video platform designed for customer interaction, visual assistance, and enterprise collaboration.
Contact us
Everything You Need to Know About Digital Sovereignty
18 Feb 2026
Learn how the PACE model helps customer service teams deliver faster, clearer support with structured, action-driven conversations.
How the PACE Model Brings Structure to Customer Service Conversations
13 Feb 2026
Learn how the GROW model helps customer service teams guide customers toward better outcomes with structured, goal-focused conversations.
How the GROW Model Improves Customer Service Conversations
5 Feb 2026
Interested in our solutions?